In the first post, we covered OAuth, OIDC and discussed how this technology was front channel (i.e. web browser) centric and some of the limitations that presented. The follow on post about GNAP, we looked at how this proposal aims to be less browser based and also mentioned some of the privacy concerns raised by having centralised Identity gatekeepers. Additionally, OAuth requires some pre-registration of client applications with the identity provider, with an issuing of client_id and client_secret (see here for more details). This has the side effect of deepening both the moat around providing Authorization Server, and also the privacy concerns and barriers to entry on becoming an Identity Provider.
In this post, we’ll look at verifiable credentials as means of overcoming some of these privacy concerns and as a gateway into the World of decentralised identity.
Verifiable Credentials are part of a suite of decentralised identity technologies that aim to address privacy concerns.
Verifiable credentials are an open standard, (backed by the Digital Identity Foundation) which provide a digitally verifiable evidence to support a claim made by a user. They are one of the dishes that comprise the buffet of technologies to support Self Sovereign Identity (aka SSI) and originate from the blockchain ecosystem (though are neither tied to or dependent on blockchain technology). First we’ll consider a concrete use case for verifiable credentials, before examining some of the aforementioned technologies and terms. One frequently cited example is around proof of academic qualifications. It goes a little something like…
…A candidate applies for a job stating that they have a university degree. In order to prove this claim around their academic achievements, the candidate presents digital evidence to the person responsible for hiring from their wallet. The evidence is a digital artefact that the candidate has received (aka been issued) by their University after graduation. Assuming the employer trusts the issuing University, then the evidence can be digitally verified. This tri-party arrangement, has the candidate as the person holding the credential, offering it to the potential employer, who acts as the verifier, as they confirm the credential is legitimate by querying the University (who is the issuer of the qualification). This whole process is termed the Triangle of Trust and is depicted below.
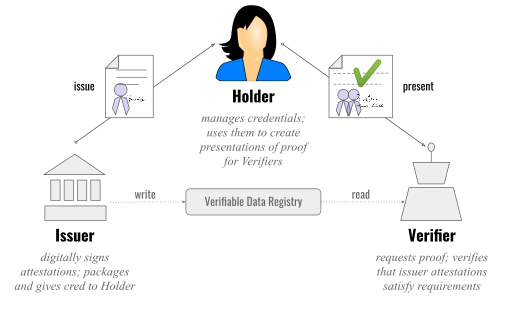
The Triangle of Trust, allows end users to retain ownership and control over their data and claims. Any party who wants to confirm a claim can do so by making a verification request against a trusted third party who issued evidence of the claim to the end user.
One of the drivers behind Verifiable Credentials is to empower the end user (or the Holder to use Triangle of Trust parlance), with possession and control over the data they share. In fact, the whole notion of users being the custodians of their own data is one of the primary drivers behind the SSI movement. When a user presents their VC backed claim to the verifying party this is termed a Verifiable Presentation. One proposal for the Verifiable Data Registry is that this could be a public tamper proof registry backed by a public blockchain, but this is not a mandatory requirement for verifiable credentials. The wallet where the end user keeps their VCs can be a device wallet (such as an Apple or Google wallet), but could be cloud storage. The definition of wallet in this sphere is intentionally loose. One additional point of note, is that Verifiable Credentials is a specification, so there are developments in leveraging the hugely successfully adopted OpenId as a transport for VCs.
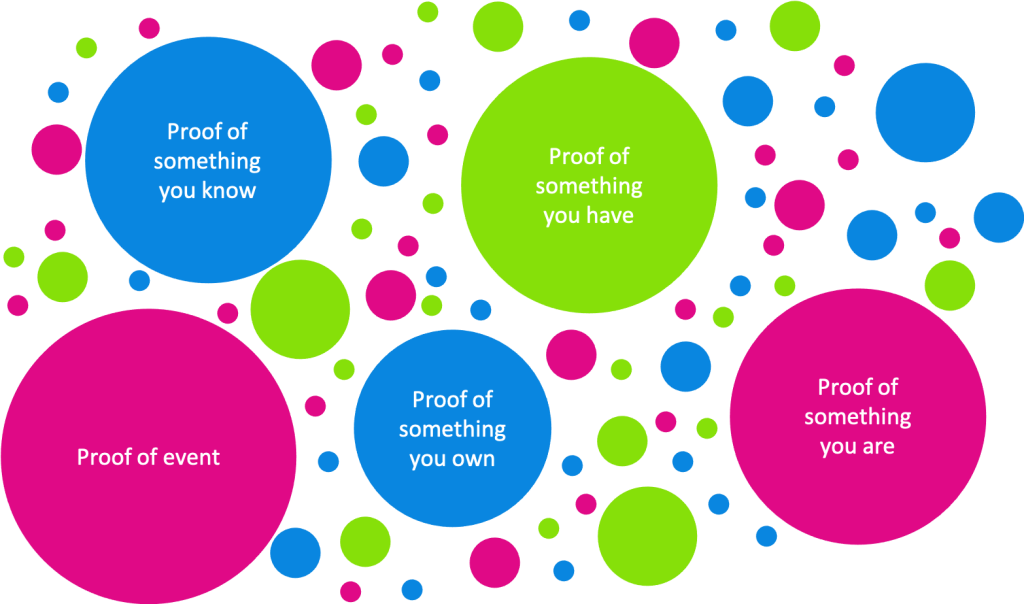
Given the flexibility of verifiable credentials (which should perhaps be more appropriately described as verifiable claims), they are able to support many different types of assertion, including MFA claims, and much broader topics too.
Verifiable Credentials can be used to establish digital trust in a range of claims, including, but not limited, to MFA claims.
(Note: Multi Factor Authentication – MFA claims, are claims regarding something the end user knows, has or is).
The recent explosion of development, comment and advances in the field of AI and Large Language Models (LLM), has led some of the industry’s leading ethical researchers to claim that this year may ring the death knoll to content based verification.
The pace of development of Large Language Models has led some commentators to describe 2023 as the year when content based verification ends. VCs may be part of the solution to address this challenge.
Considering the concerns around content based verification in the future, could VC and presenting verifiable claims be the future of Trust and Identity? Or one of toolkit of components in enabling digital trust? And how to manage any disconnected islands of Trust, given the model appears to hinge on having pre-approved issuers?
There are still open question about the operational support for Verifiable Credentials, such as how to support lost credentials/wallet access in a robust and reliable manner.
The flexibility of Verifiable Credentials suggests they can also be used to endorse events, which is a neat segue into our next post, where we look at shared signals as a mechanism to share messages between parties.
See also:
- W3C VC data model
- https://verifiablecredential.io
- Identity Foundation
- SSI book by Manning